More than a year since the “Women, Life, Freedom” protests, the Miaan Group has uncovered that hackers, with ties to Iran, are conducting an unprecedentedly broad and coordinated campaign of impersonation and phishing. This campaign is aimed at civil society targets, affecting individuals both within and beyond Iran’s borders.
In 2023, Miaan released a report that investigated and documented more than a hundred cyberattacks targeting journalists, civil society activists, and advocates for the rights of ethnic and religious minorities..
While conducting this research, Miaan Group observed that the effectiveness of the impersonation and phishing campaign targeting civil society figures and organizations, as outlined in our November 30 report, has encouraged cyber operatives aligned with Iran to adopt these tactics on a broader scale.
Miaan’s findings show that the hacker groups engaging in impersonation and phishing are backed by the Iranian government. These actors impersonate real people employed at credible international think tanks and institutions to communicate with their victims. A report by Microsoft refers to this same tactic.
Executive Summary
The tactic employed by the attackers consisted of impersonating a real person working at a credible organization to start a conversation about a fabricated event, closely resembling a real, documented case. After winning the subject’s trust, the attackers sent them a phishing link with a manipulated name.
The attackers did not rest with the target’s personal information. After gaining control of the victim’s email account, they sent emails with a phishing link to others in their network to access those contacts’ information in turn.
Key Findings
- The cyberattacks were directed at a human rights and education group. This group is known for conducting classes on civil, labor, and human rights, catering to the general populace and civil activists, some of whom may be located in Iran.
- The attackers made use of social engineering. They sent convincing and meticulous messages in English to lure victims. The individuals they impersonated were real, and discoverable through internet searches. The references made in their messages were accurate, and the events in Iran they referred to were relevant, understandable, and convincing for targets.
- The attackers timed their actions carefully. They sent similar messages to every member of the organization on a Saturday, a day when victims were less likely to communicate during typical business hours to collectively devise a response.. This timing allowed the attackers to exert emotional pressure about the false scenario they depicted to convince the victim to click the phishing link (presented as, for example, “a Google Drive containing information”).
- These attacks confirm previous findings that Iran has improved its open-source intelligence operations. The attackers researched their targets and found information such as names, institutional affiliations, activities, and interests. They then used this to craft more effective and convincing attacks. In Microsoft’s recent report, Iran was named as one the countries (beside Russia, China, and North Korea) accused of using LLM artificial intelligence to identify the jobs, locations, and relationships of dissidents.
- The attackers first used WhatsApp to initiate communication with the victim. After this victim was hacked, they followed up with others in their contact network by way of email.
- After hacking the victim’s account, the attacks attempted to access other accounts connected to it. They were thus able to access the victim’s LinkedIn profile.
Incident Analysis
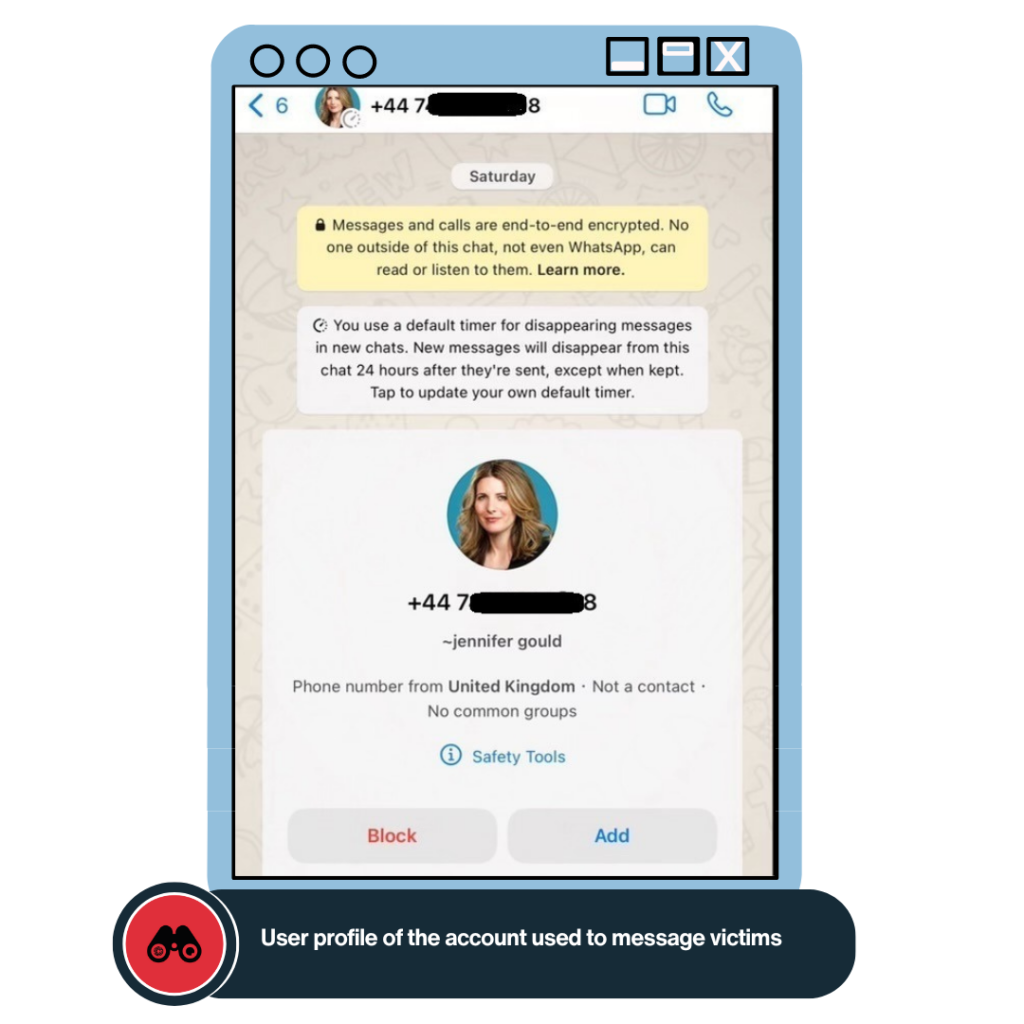
On January 9, 2024, an individual purporting to be “Jennifer Gould” sent a message to most of the members of an educational organization. They claimed to have received medical information from sources in Iran about a 21-year-old girl who had been seriously physically abused by Islamic Republic forces. The individual introduced themselves as a member of RAND, and said they wanted to share the information with the recipients.
When we searched “Jennifer Gould” online, we found the details of a real individual employed by RAND (a non-profit research organization based in the US). Available information indicates Ms. Gould is Vice President, Chief of Staff at RAND.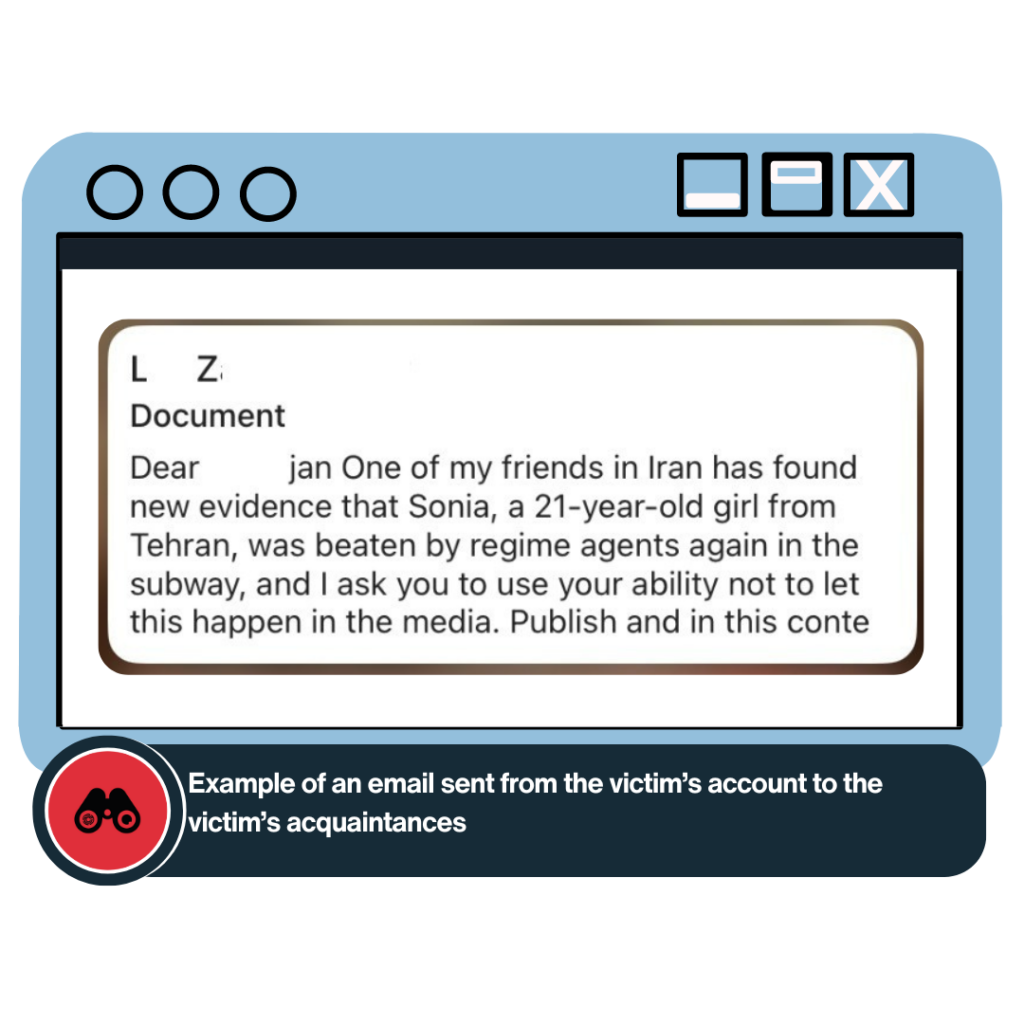
In their fabricated account of the physically abused girl, the attackers borrowed from the story of Armita Geravand, implying an association without referring to her directly.
The attackers used a phishing link that appeared to belong to a Google Doc to show that it was safe. In this way, they were able to deceive their victim and gain access to their email.
After accessing the victim’s email, the attackers tried to gain entry into accounts associated with it. They were able to hack the victim’s LinkedIn page in this way.
An investigation of the device connected to the LinkedIn account before it was secured, as well as an investigation of the phishing link, showed that the attackers used a shared “IP range” – a common location and device – to access and hack the victim.
After gaining access to the victim’s email account, the attackers sent similar messages to everyone in their network. The messages told of an injured 21-year-old girl, and the attackers claimed to have documents pertaining to her hospitalization.
A phishing link accompanied the message. In this round, the attackers impersonated the initial hack victim, whose familiarity to the second set of targets increased chances of success.