With the onset of Israel’s military attack on Iran on June 13, 2025, Iran entered one of its most severe and targeted periods of communication disruption and information censorship in its history. Leveraging its experience from the November 2019 internet shutdown and the development of infrastructure and policies related to the “National Information Network,” the Iranian government this time completely blocked not only outbound communications but also inbound international internet traffic to the country.
During this process, starting from June 18, certain websites and specific service platforms were added to a whitelist, allowing access to them from outside the country. Some news websites have so far been included in this list, while others are still awaiting review. This approach demonstrates a selective and managed filtering of both inbound and outbound internet traffic—a situation in which the government decides what can and cannot cross its digital borders.
Key Developments
- Complete Internet Blackouts, Including SSH Ports: The internet was entirely cut off for extended periods, including the blocking of SSH ports, which were previously used to maintain some level of access.
- Incoming Internet Traffic Blocked: Unlike the November 2019 shutdown, incoming international internet traffic was also completely blocked. Even data centers that remained connected in 2019 were entirely cut off this time.
- Access Limited to National Information Network (NIN): Access was strictly limited to Iran’s domestic “National Information Network” (NIN).
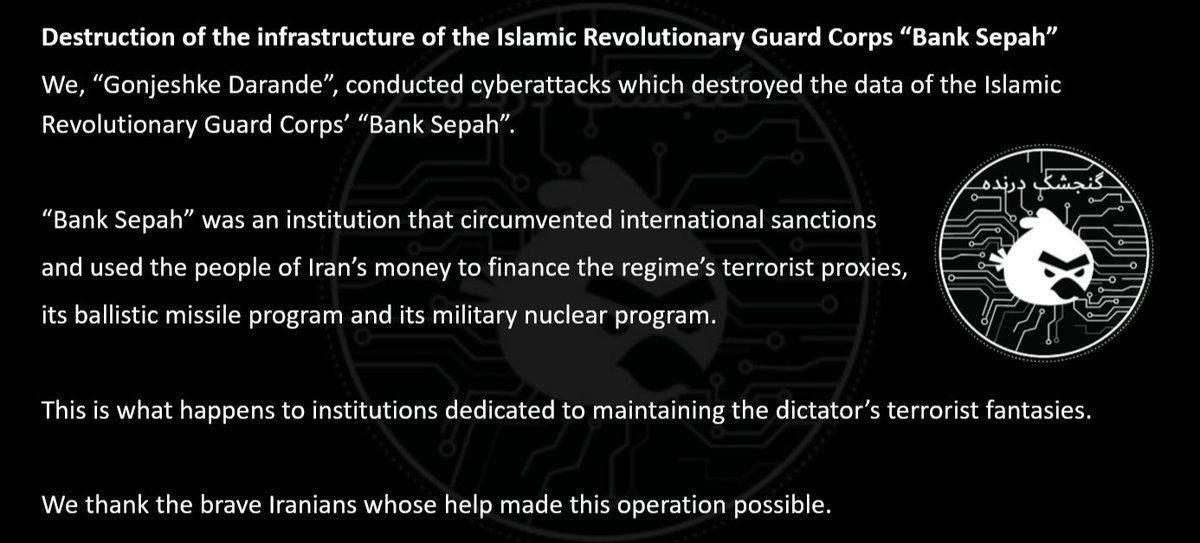
- Severe Disruption to Banking and ATMs: The banking systems and ATMs experienced serious disruptions. Rumors of cyberattacks on banks circulated, including a claim by the group “Gonjeshke Darande” (Predatory Sparrow) of hacking and deleting data from Bank Sepah.
- Google Maps and GPS Issues Amid Fuel Shortages: Disruptions to Google Maps and GPS led to people getting lost while trying to leave cities, compounded by existing fuel shortages.
- International SMS, Calls, and VoIP Disrupted: Inbound SMS messages and calls from outside the country were cut off, and VoIP tools experienced disruptions due to heavy pressure.
- Galaxy Store and Google Play Inaccessible: Both the Galaxy Store and Google Play became inaccessible, preventing users from downloading applications.
- Official Announcement on Hijab Fines: The government officially announced that fines related to improper hijab had been sent in error and would not be enforced.
- Furthermore, security warnings to citizens increased including messages about the risk of mobile phone explosions—a possible reference to events in Lebanon.
Social Transformations
- Unlike previous internet shutdowns, this time we’re seeing public campaigns encouraging migration to domestic applications like Bale, Rubika, Virasty, and iGap. This development points to a mix of fear, communication breakdown, and an effort by people to maintain family contact.
- For the first time, some ordinary users, alongside the government, have encouraged people to use these domestic applications.
- Many people have tried to offer shelters for war refugees and displaced individuals using social media (during the limited hours when connection was possible), but internet disruptions have prevented this information from being properly disseminated.
Technical and Cyber Movements
- There are reports of a cyberattack by the group “Savage Sparrow” on a cryptocurrency exchange, resulting in the deletion of all stolen assets.
- Rumors about the possibility of accessing Starlink with a mobile application have emerged. This has raised concerns about the spread of malware and social engineering, similar to what was observed during the “Woman, Life, Freedom” protests.
- The Revolutionary Guard Corps has claimed that Israel is using Starlink to guide drones. This accusation could unfairly increase the risk of internal users being accused.
Operator Status and Access
- Kermanshah Province is almost entirely cut off from the internet.
- Rightel has remained relatively stable.
- E-sim cards from Turkey, the Emirates, and Vodafone Italy worked until the fourth day of the conflict, then stopped functioning.
- Hamrah-e Aval (MCI) is largely out of service, and Irancell is operating unreliably.
- Landline phones have also been mostly deactivated.
Day 1 of the Conflict: Friday, June 13 | Beginning of Widespread Disruption
Starting Friday morning, June 13, users reported the complete blocking of WhatsApp messenger and severe disruptions to VPN functionality. Data released by Cloudflare also confirmed a sudden and significant drop in international internet traffic, a clear sign of the onset of widespread filtering and targeted restrictions.
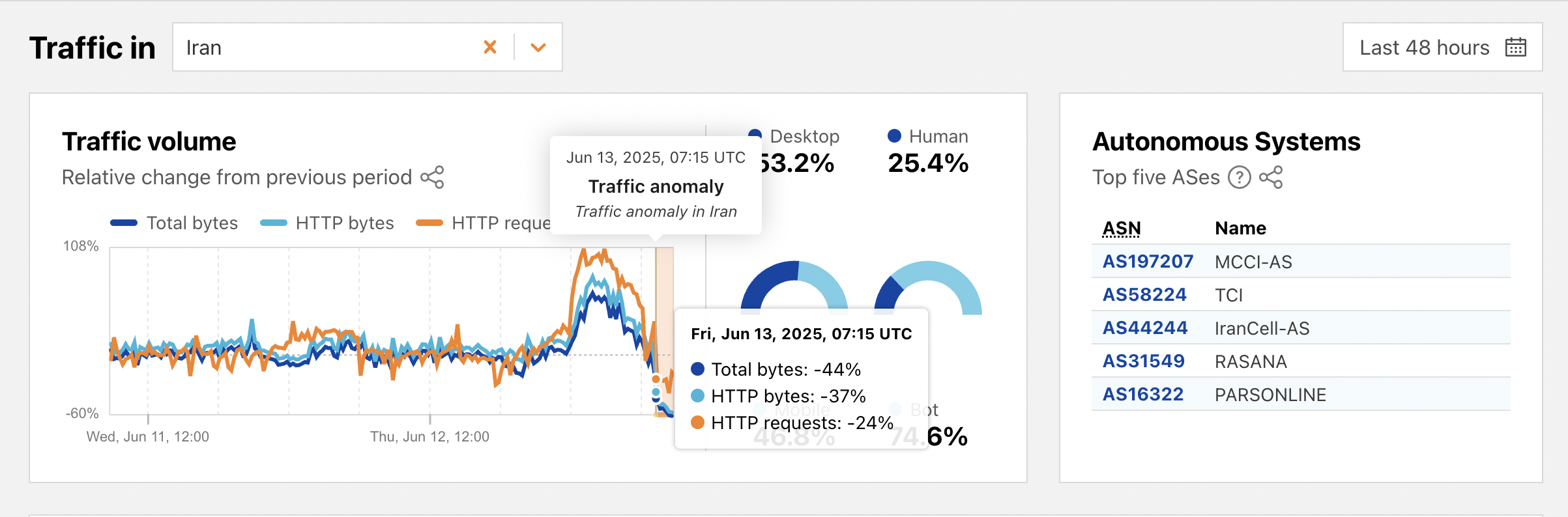
ArvanCloud Radar also reported severe disruptions in various data centers across the country, particularly those of Hamrah-e Aval, Pars Online, Afranet, and HostIran. These disruptions began around 9:00 AM Iran time and peaked between 10:30 and 11:00 AM Iran time.
At the same time, the Ministry of Communications issued an official statement announcing that, due to the country’s special circumstances and based on decisions by relevant authorities, “temporary restrictions” had been imposed on the national internet. Alongside this statement, judicial and military warnings prohibiting the photographing of missile movements intensified concerns about a complete internet shutdown.
Simultaneously, unidentified calls from neighboring countries, including Iraq and countries bordering the southern Persian Gulf, were made to citizens. These calls featured recorded messages declaring a state of emergency and urging people to stock up on items such as water, flour, and cash.
Day 3 of the Conflict: June 15 | Regional Communication Collapse
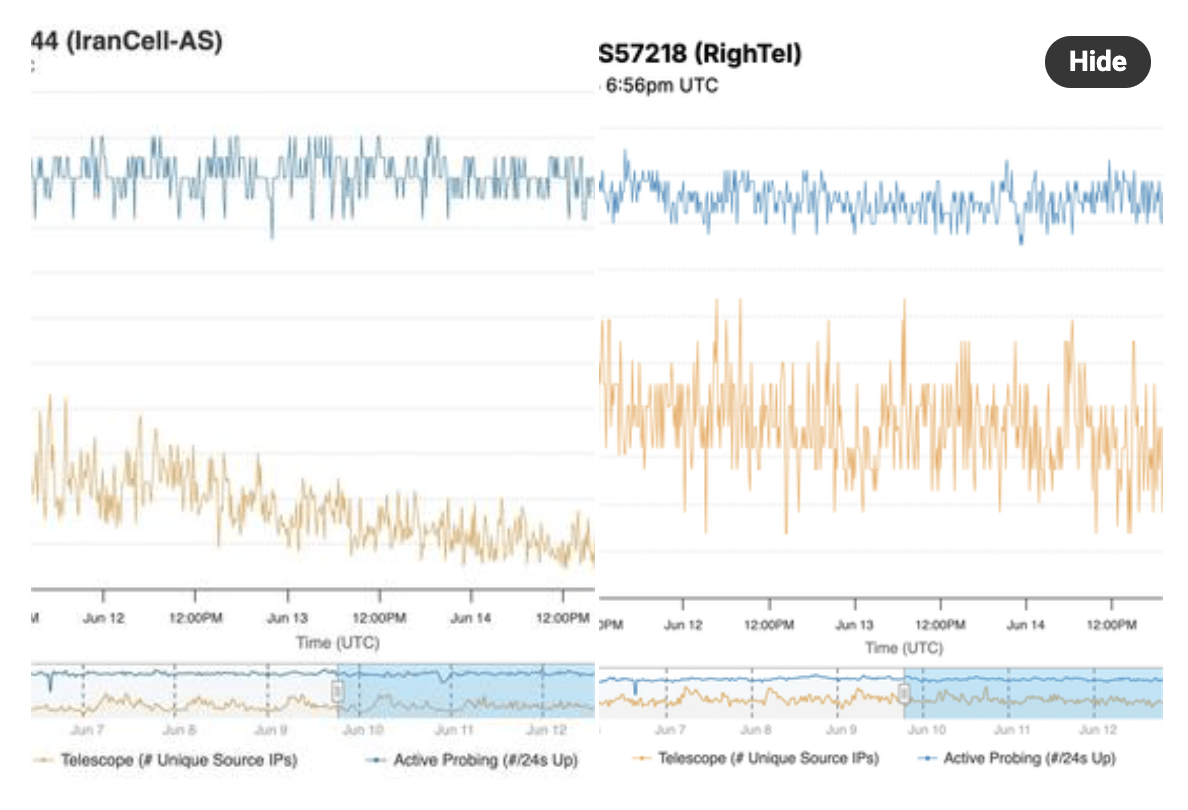
IODA data has confirmed a drop in connectivity for Irancell (AS44244) and Rightel (AS57218) mobile networks:
In the published charts, both key indicators—Active Probing and Telescope—show a decreasing and unstable trend for both operators starting from June 15. This situation indicates that these operators have experienced severe disruptions in international data exchange and responsiveness to external networks.
In addition to the disruptions in mobile operators, most landline phones were also cut off. According to user reports on social media, some digital SIM cards from outside Iran with roaming service were able to provide uncensored internet to users inside the country. This pathway, however, soon became unavailable in the following days.
Day 4 of the Conflict: June 16 | Official Announcement of Speed Reduction
The government officially acknowledged and justified the intentional reduction of internet speed, attributing it to efforts to counter “cyberattacks.” This effectively elevated the issue to an official policy.
Meanwhile, rumors began circulating about accessing Starlink internet via a mobile application, raising concerns among internet security experts about the potential spread of malware, similar to what was observed during the 2022 protests.
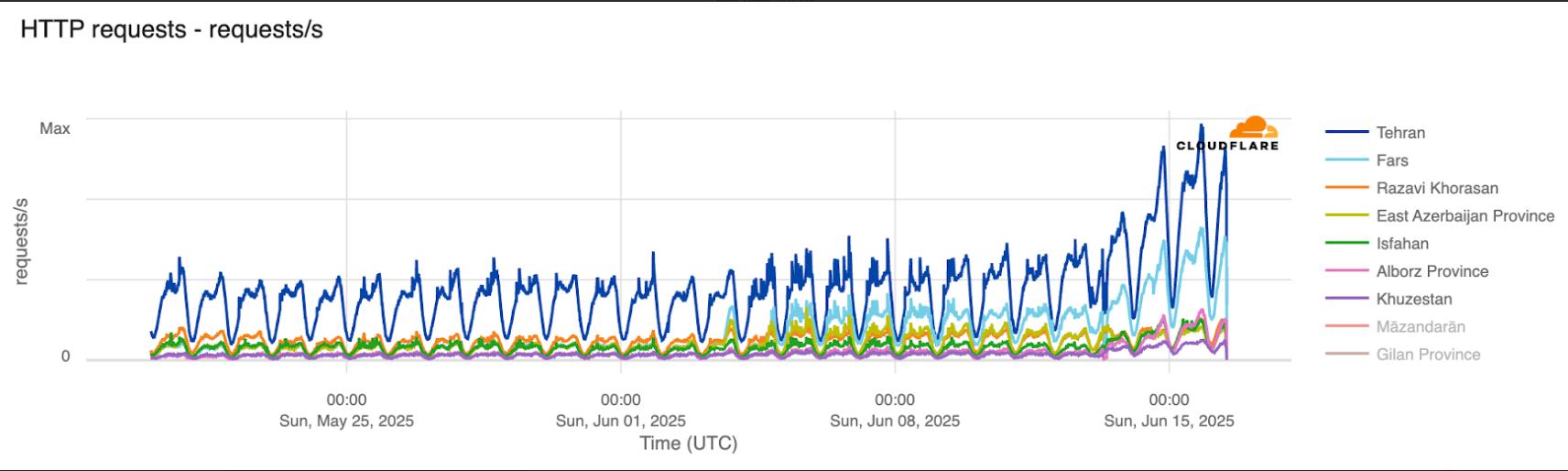
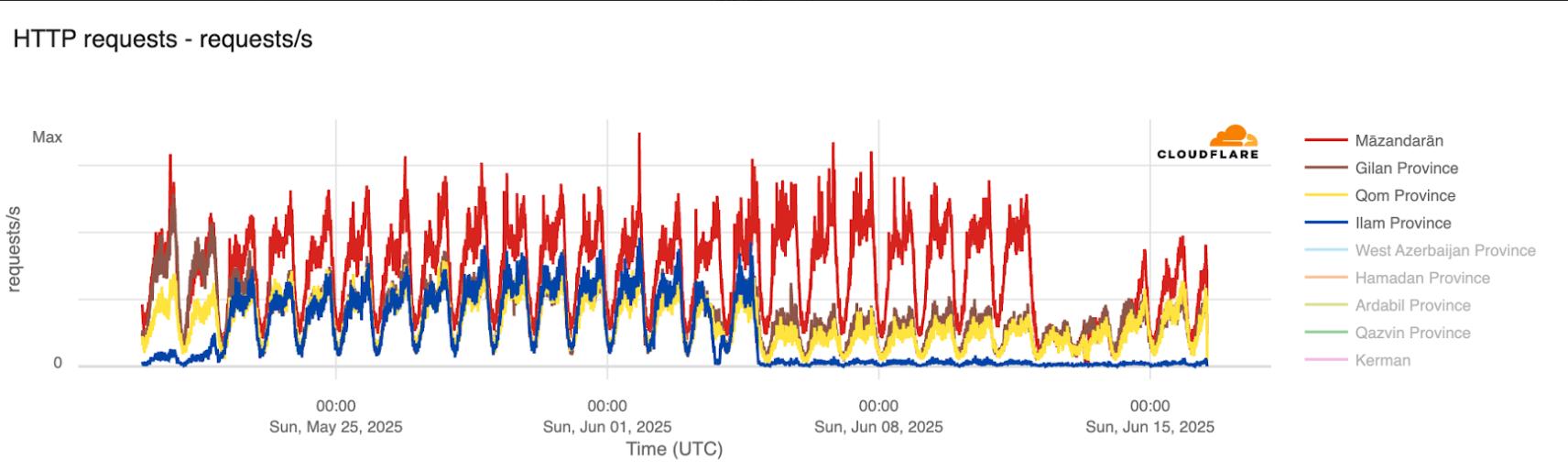
While a significant decrease in HTTP request rates had been observed since June 14, by June 16, Cloudflare data revealed a notable shift in HTTP traffic patterns across various Iranian provinces.
Mazandaran province, which previously had the highest traffic, recorded a significant drop on June 15 and 16. In provinces such as Gilan and Ilam, traffic patterns appeared to be fluctuating and unstable.
On the other hand, Tehran province maintained the highest volume of traffic and even experienced a relative increase in requests from June 14 onwards. Fars and Razavi Khorasan also showed more traffic stability compared to other regions. These disparities could indicate the imposition of regional restrictions or the shifting of traffic load to main data centers.
While the HTTP request charts recovered in some areas, byte-based indicators remained low. This suggests that despite requests being sent, received responses were limited, and connection quality remained poor. Therefore, Cloudflare data indicates widespread yet regionally asymmetrical internet disruption in Iran on June 16. Central provinces experienced more stable conditions compared to northern and western regions.
The persistent decrease in transferred data volume (despite increased requests) could signify bandwidth throttling or the blocking of external responses.
Day 5 of the Conflict: June 17 | Crisis Peak and First Widespread Internet Blackout
According to Cloudflare data, from 5:30 PM Iran time, the internet in Iran was virtually cut off. Outbound traffic from the country plummeted by 75%, leaving only the National Information Network accessible.
Hamrah-e Aval and Irancell were completely cut off, with limited connections only being restored around 9:00 PM local time.
Following this, in a rare move, a group of users, contrary to past behavior, began promoting domestic applications like “Bale” – not out of trust, but out of desperation to maintain contact with loved ones. Reports of emails inviting users to install these apps circulated, which analysts interpreted as part of preparations for a complete transition to the domestic network.
From a technical standpoint, reports indicated the blocking of SSH ports, the unavailability of the Samsung Galaxy Store, disruptions in the banking network, and the complete cessation of Google Maps functionality. On the same day, Bank Sepah was targeted by a hacking attack. The “Gonjeshke Darande” (Predatory Sparrow) hacking group announced the attack, claiming to have deleted all of the bank’s data. Domestic media, while confirming the Bank Sepah hack, warned that due to the bank’s support for gas stations, fuel pumps might also experience disruptions. Following this hack, Bank Pasargad, a subsidiary of Bank Sepah, also experienced disruptions, which persist as of the publication of this report.
The Revolutionary Guard Corps also, for the first time, issued a warning regarding the use of Starlink technology within the country, claiming that Israel is utilizing Starlink to guide its drones.
Day 6 of the Conflict: June 18 | Second Widespread Internet Blackout
On this day, the second major internet outage of the war occurred around 4:30 PM Iran time.
A large number of internet service providers in Iran experienced a complete loss of international connectivity.
According to IODA data for this day, not only did mobile operators face disruption, but international traffic, Google searches, and network probe responses also dropped to near zero.
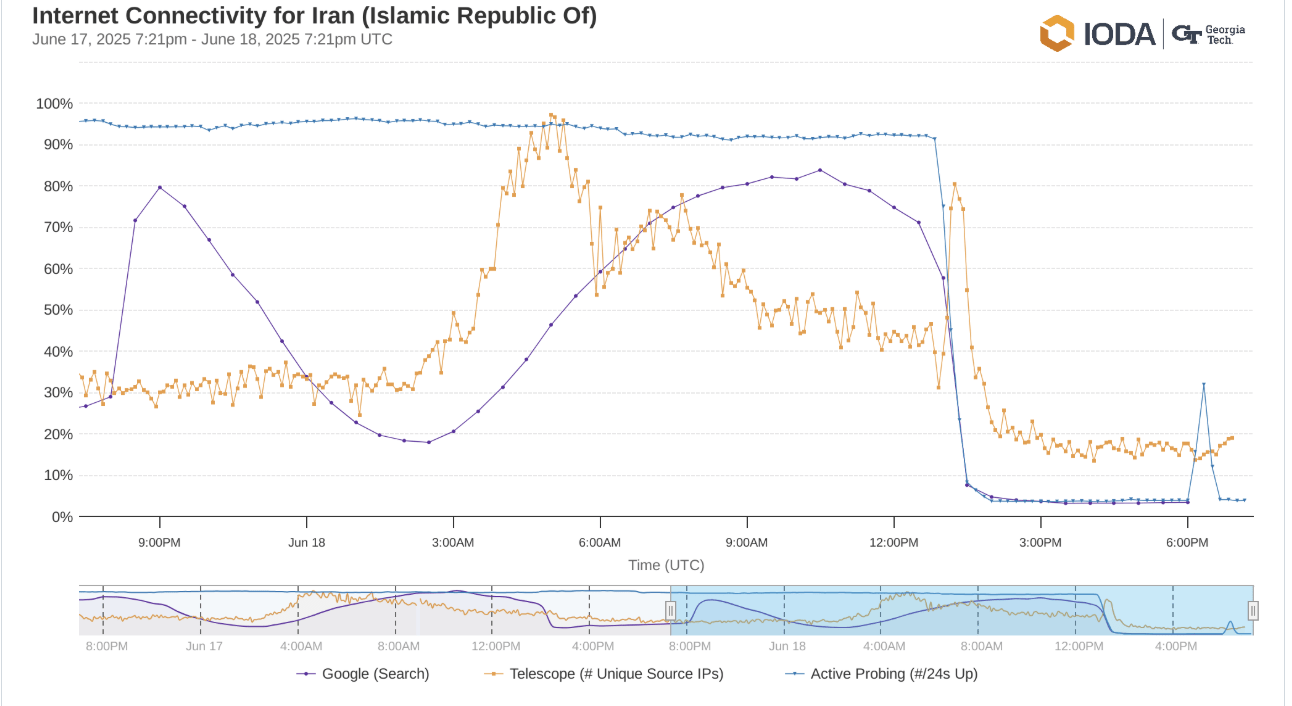
The Telecommunication Company of Iran (TCI) network, which had been active the day before, was completely cut off on June 18. TehranServer data center, which provided services to a significant number of websites and users, also lost its connection.
Many users reported that internet access was completely cut off for about an hour, with only the National Information Network remaining active. VPN access was severely unstable or impossible in many areas, and VPS providers announced their inability to accept new orders due to “unprecedented request volumes.”
In the late hours of June 18, reports emerged indicating that Iran’s internet traffic had plummeted to near zero. Real-time data from Cloudflare and Google showed that international internet access was virtually severed, and inbound and outbound traffic from the country was severely restricted or halted. Based on data obtained from some network monitoring systems that operate by monitoring internal-to-internal communications, from 12:00 PM to 5:45 PM Tehran time on June 18, evidence of severe fluctuations and instability in the quality of internal communications within Iran was observed. This data indicates that even within the domestic communication infrastructure, there were noticeable disruptions and instability. Such fluctuations might have negatively impacted access to national services, messaging apps, and internal systems. During this period, several sudden spikes in latency were recorded, indicating a decline in network performance even at the domestic level. Specifically:
- At 12:35 PM, response time increased to approximately 450ms.
- At 5:25 PM, the highest latency, around 800ms, was reported.
- At other times, the average network response was between 250 and 350 milliseconds.
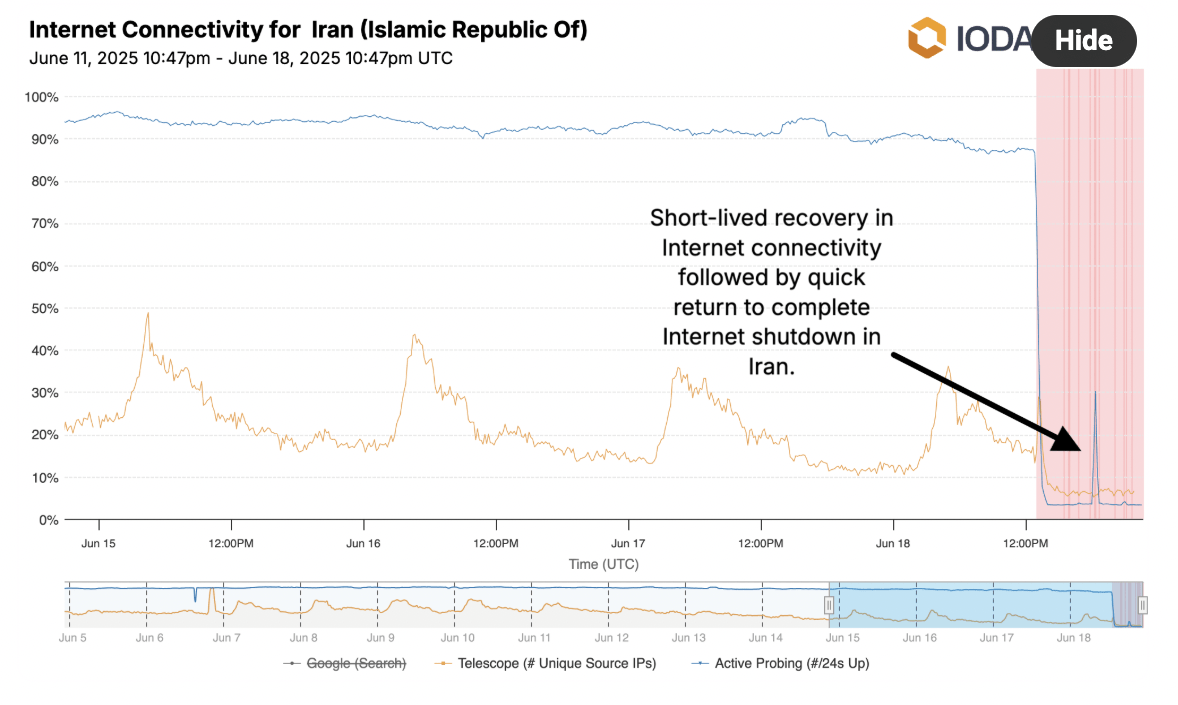
Cloudflare and IODA data showed that some Iranian internet networks briefly returned to an active state around 9:30 PM Iran time, but then connectivity reverted to a complete shutdown:
Google traffic data also indicates that the sharp decline in traffic for Hamrah-e Aval and Irancell peaked notably on June 16. Subsequently, a recovery trend began from June 17 onwards, though it has not yet returned to pre-disruption levels. Only limited or intermittent connectivity has been established for some users in specific areas.
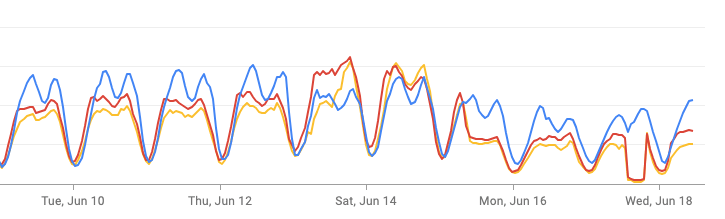
While many of Iran’s internet networks faced widespread outages or severe drops in international traffic on June 18, IODA data indicates that some networks exhibited different performance.
Specifically, the Tebyan network (AS48434) did not experience a complete shutdown and maintained a level of international traffic. In the Cloudflare chart, although a noticeable drop in transferred data volume (Total bytes and HTTP bytes) is observed from June 13, this drop does not reach zero, and relative activity is still visible on June 18. It can be concluded that Tebyan was “not affected by the complete blackout on June 18.”
On the same day, in the evening hours, the Ministry of Communications and Information Technology issued a statement claiming that, due to the “enemy’s” misuse of the country’s communication network for military purposes, temporary restrictions had been imposed on users’ access to the internet. However, it asserted that access to public communication services and domestic service platforms remained available. This statement contradicted the earlier declaration by Fatemeh Mohajerani, the government spokesperson, who at 2:00 PM local time, on the same day had stated that the internet would not be nationalized unless there was an emergency.
Simultaneously with the official confirmation of internet disruption by the Ministry of Communications and reports of limited user access to the global network, news broke of online and satellite services of the Islamic Republic of Iran Broadcasting (IRIB) being hacked. At 8:00 PM Tehran time, IRIB’s programming was interrupted, and the message “Rise up, this is your moment” appeared on screen.
This type of cyberattack on official state media, amidst widespread internet disruption and regional conflicts, underscores the intense security and information-related tensions within the country.
Following the hack of some IRIB services, and from approximately 9:00 PM Iran time, based on data from internet monitoring systems including IODA and Ainita, it was reported that some domestic data centers and online services were returning to an active state.
Simultaneously, a “security” warning was issued by government-affiliated sources, claiming that 19 commonly used VPN services could pose a security threat to users. The warning stated that some of these applications have “suspicious access” and might collect users’ personal data. It was also alleged that some of these VPNs are associated with companies attributed to or linked with “Zionist regime” entities. The list of these VPNs includes widely used services such as ExpressVPN, NordVPN, TunnelBear, Surfshark, Psiphon, Hotspot Shield, Mullvad, and several others. This warning could be part of a coordinated government effort to reduce the use of circumvention tools and pressure users of these tools.
Meanwhile, the hacking group “Savage Sparrow” announced that it had hacked a cryptocurrency exchange and deliberately destroyed all stolen assets.
Concurrently, reports were circulating that some international social media platforms had removed posts by Iranian users critical of Israel. This issue is currently under investigation by digital rights activists.
Domestically, numerous official and unofficial emails and messages from various entities and unknown individuals are being disseminated, urging people to migrate to government-approved applications like “Bale.” More shockingly, some ordinary citizens have spontaneously launched campaigns encouraging others to use these platforms – an unprecedented behavior compared to past internet outages, which were always met with general distrust of these tools.
However, it must be considered that in wartime conditions, when survival becomes the priority, issues like “security” will become less important. Some online activists have stated that what years of government efforts to promote domestic messaging apps failed to achieve is now occurring under the shadow of war and a security crisis.
Day 7 of the Conflict: June 19 | Continued Widespread Internet Blackout
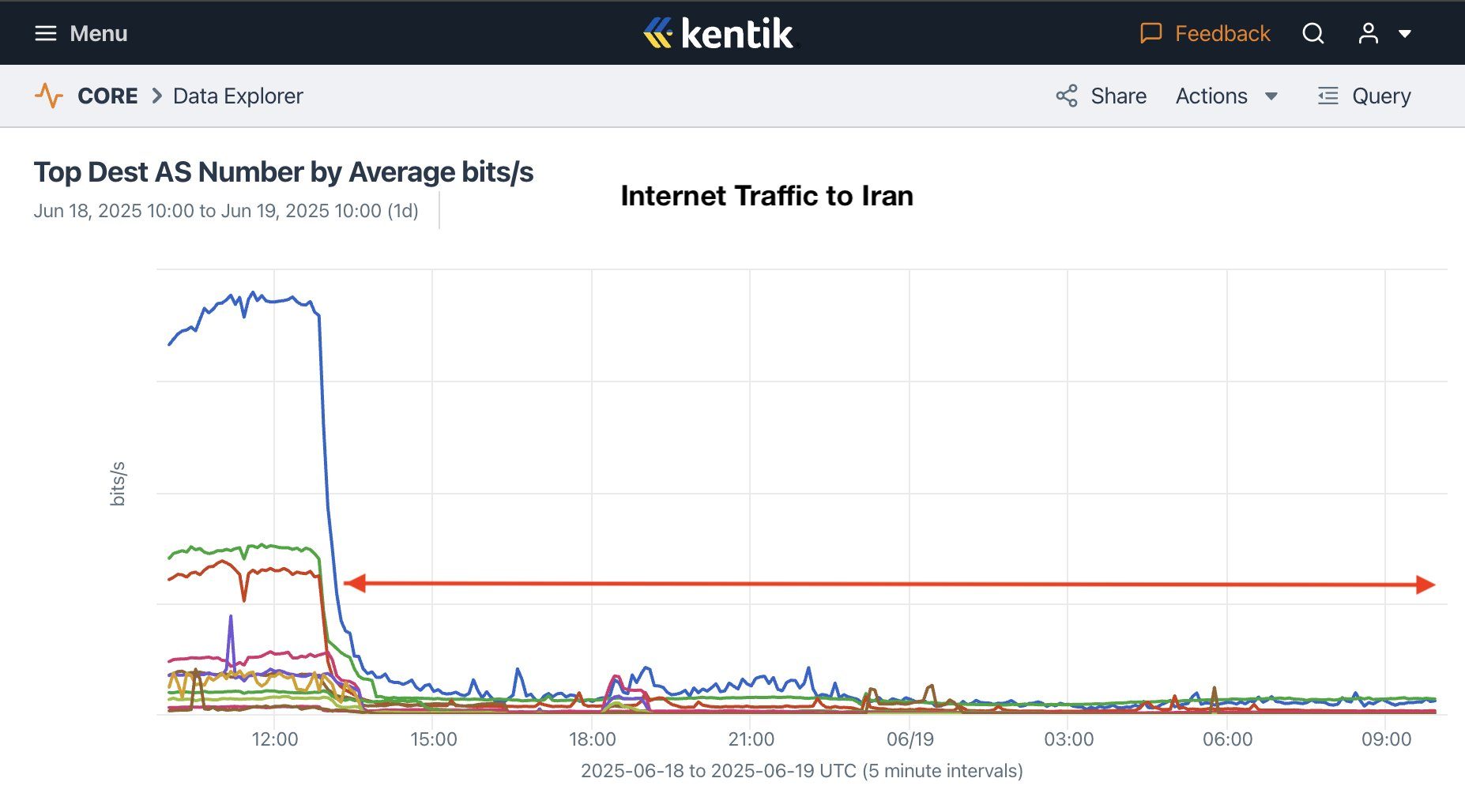
The second day of widespread internet disruption continues. Kentik charts indicate that inbound traffic to Iran was virtually zero between 4:30 PM (local time) on June 18 and 1:30 PM (local time) on June 19:
According to some reports, Iran is implementing a process in which only government-approved websites and services will remain accessible from outside the country. In other words, a “whitelist” is being compiled that will include sites and services deemed permissible for international communication by the government.
Some news websites have already been placed on this list, while others are still awaiting review.
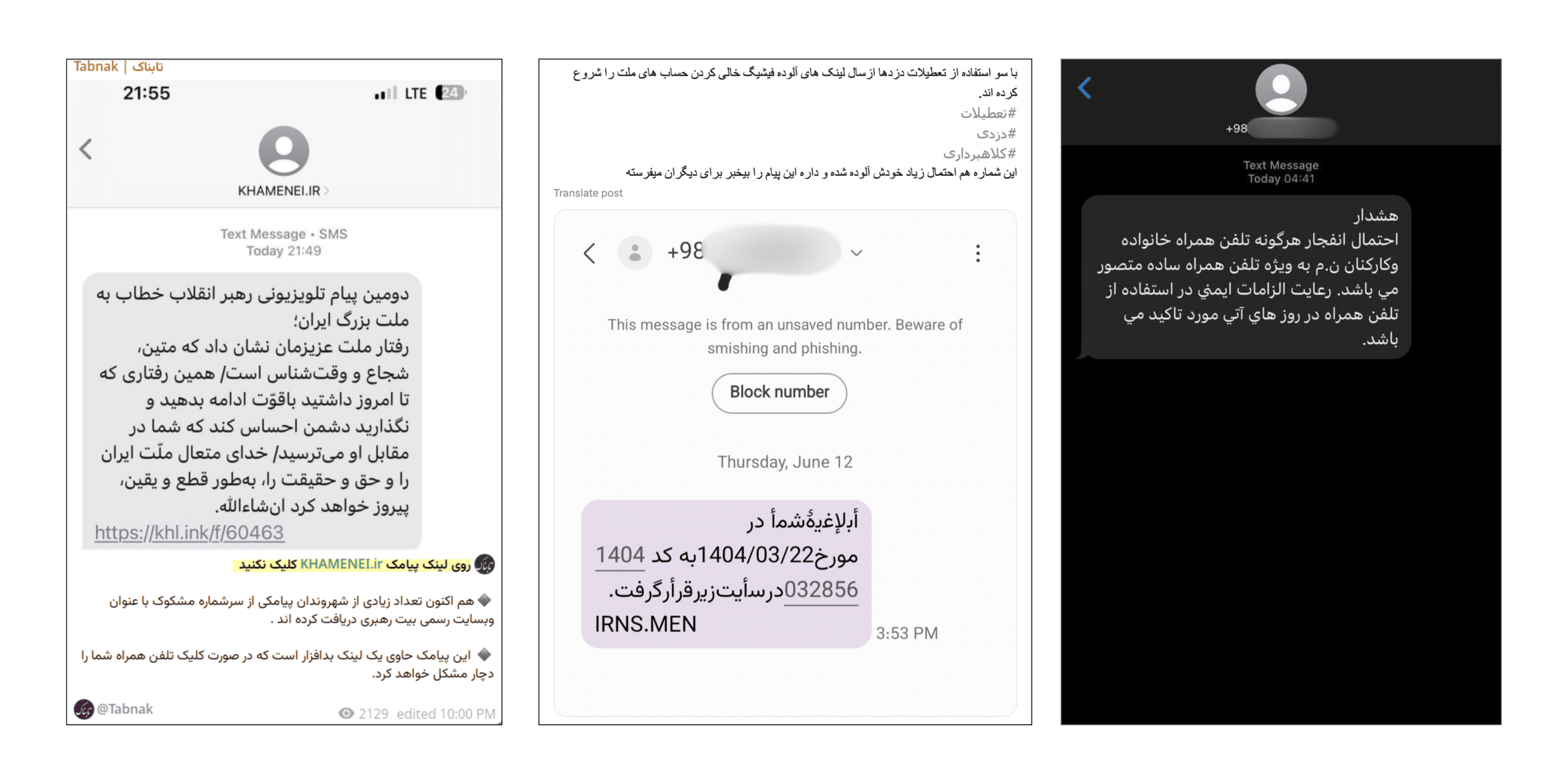
On the seventh day, amidst widespread internet and communication disruptions in the country, a number of social media users and some media outlets warned about the widespread dissemination of SMS messages containing malicious links.
These SMS messages range from warnings about the potential explosion of military personnel’s and their families’ mobile phones to messages with emotional or security-related themes, all attempting to lure users into clicking on specific links. Some of these messages have been sent under the names of official bodies or with language similar to government communications.
Tabnak media also reacted to these incidents, warning: “Do not click on the KHAMENEI.ir SMS link.”
Reports indicate that clicking on these links could lead to mobile phone infection and the theft of users’ personal or banking information.