In the past month, Iranian officials—from Majles representatives to cabinet ministers and members of the Supreme Cyberspace Council—have repeatedly pointed to circumvention tools as a major source of problems and insecurity in cyberspace. These developments suggest that Iranian officials see themselves as at war with these technologies and are planning accordingly.
Though such comments have precedent, it seems the new wave has been triggered by a recent report from the Communications Infrastructure Company. The report stated that in the 21-month period ending in summer 2024, it logged more than 430,000 DDOS attacks, 65% of which originated from infected devices or bot pools.
Minister of Communications Sattar Hashemi has also joined the chorus of criticism of circumvention tools. According to Seyyed Javad Hosseini Kia, deputy Chair of the Majles’ Industry Commission, Hashemi said such software was indefensible while advocating for his agenda in meetings with the Majles. “Cyberattacks have intensified because of the use of circumvention tools,” Hashemi said.
Article 6 of the Directive to Investigate Methods of Increasing Domestic Traffic Share and Combatting Refinement-Breaking Tools (issued by the High Cyberspace Council) states that “the use of tools to break refinement is prohibited, except for those instances permitted by law.” Given this, it appears that Iranian officials are preparing to act against circumvention tools in a serious way.
Mohammad Amini Aghamiri, head of the National Cyberspace Center, has recommended two methods to reduce the use of circumvention tools in line with the aforementioned directive.
Aghamiri believes that either 1) private companies should negotiate with filtered platforms to offer filtered content with mediation, or 2) these companies should create an intermediate utility between users and filtered content to deliver only government-approved content to users.
Though Aghamiri gave no examples, Filterwatch highlighted one such technique in its April 25, 2024 report entitled “Next-Generation Filtering: Phishing and Other Governable Models.”
The technique – very similar to the one outlined by Aghamiri – involves a fraudulent copy version of a service or site based outside Iran, which uses an intermediary to receive, investigate, and where necessary censor user requests before sending them to the primary service. Upon receipt, it also censors the primary service’s response before making it available to the user.
Network Access
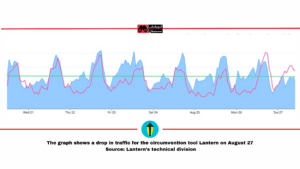
On August 27, Iran’s communications network suffered general disruption. According to reports received by Filterwatch, users of Hamrah-e Aval and Iran Cell had severe difficulty connecting with circumvention tools from 1:30 PM local time.
Figures provided to Filterwatch by the technical division of the circumvention tool Lantern also show a pronounced drop in traffic from this service’s users during the same period.
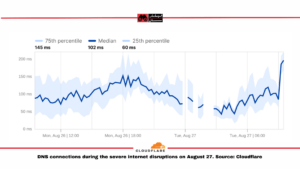
Meanwhile, Cloudflare data indicates that HTTP protocol traffic,used for web browsing,as well as DNS contact, was disrupted at this time. Iran Cell and Hamrah-e Aval, Iran’s two main cell operators, also suffered big drops.
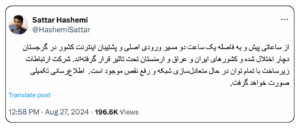
Minister of Communications Sattar Hashemi confirmed this disruption in a Twitter post, calling it a result of disturbances to the primary incoming internet lines running through Georgia. The disruptions also affected Armenia and Iraq, Hashemi said.
Further investigations by Cloudflare Radar show that IPs registered in the communication spaces of Armenia and Georgia suffered disruptions at this time, indicating severe disturbance verging on total outage.
On August 13, Shahryar Datashare (which belongs to ArvanCloud) experienced disruption, likely owing to an electrical outage. ArvanCloud owns 59% of Iran’s cloud service market, and disruptions to the company have a big effect on users. Disruptions due to electrical outages have struck data centers since last month, and Regulatory Organization head Amir Lajevardi confirmed the outages had affected users of both cell and landlines.
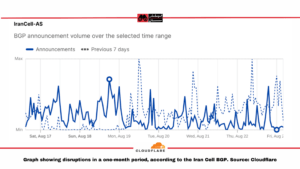
According to Arvan Cloud Radar and Cloudflare Radar, Iran Cell’s data center experienced disruptions most days of the past month. Filterwatch’s field investigations inside Iran show that from at least August 22, disruptions to network protocols caused problems for Iran Cell users attempting to connect to the circumvention tool OpenVPN.
The winter 2023-2024 report from the Regulatory Organization shows that Iran Cell controls 42% of the mobile internet market in Iran. Additionally, mobile internet users grew more rapidly than landline-based users during that period. This suggests that the Iran Cell disruption impacted nearly half of all internet users in the country.