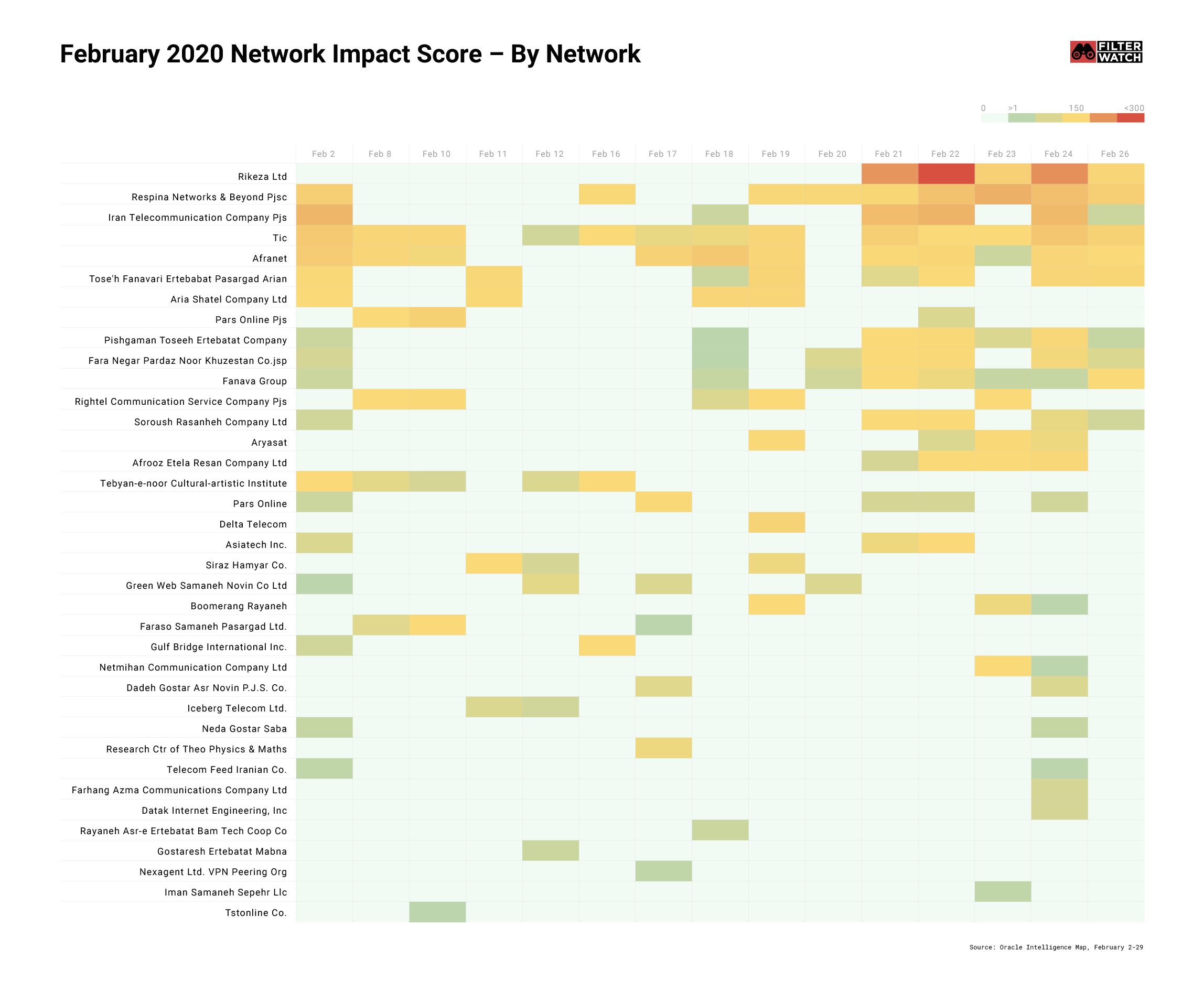
Unlike in January — where we saw a number of sustained internet disruption incidents, and in some cases even shutdowns — we did not see any protracted internet shutdowns in February. However, we were able to observe a number of network disruptions affecting Iran, commencing from 2 February.
In contrast to January, much of the disruption was short and at times specific to geographical locations. While Iranian officials claim that some of the disruptions were the result of DDoS attacks, they have so far failed to provide any convincing evidence or supporting data.
We believe a number of disruptions observed during this period were caused by authorities’ introduction of a new Internet Exchange Point (IXP) named ‘Rikeza Ltd’. Again, Iranian authorities have failed to publicly acknowledge this, or to provide a public explanation about its creation.
On 8 February, the Director of the Telecommunications Infrastructure Company (TIC) Hamid Fatahi claimed on Twitter that DDoS attacks from outside Iran were the cause of network disruptions. He tweeted:
“Hired hackers today launched the most widespread attack against the country’s infrastructure in Iranian history. Millions of origins targeted millions of destinations and are seeking worldwide disruption to Iran’s Internet network with a SYN [synchronised] flood* attack of 180 million PPS [packets per second]. The attack was repelled, and their efforts were futile.”
*[A SYN flood is a form of DDoS attack in which an attacker sends a succession of SYN requests to a target’s system in an attempt to consume enough server resources to make the system unresponsive to legitimate traffic.]
Our research was unable to prove such a claim. However on February 17, Sajjad Bonabi — a TIC board member who previously confirmed the DDoS attack on Twitter — said the source of the DDoS attack originated from inside the country, and suggested that it was launched by “domestic competitors”.
Detailed documentation of our findings and observations from February are available below. Let our team know if you have any questions or observations of your own.

2 February — Disruptions noted across 13 providers
We observed disruptions on at least 13 providers. Oracle Intelligence Map (OIM) data confirmed these disruptions, which primarily affected Fars Province, Khuzestan Province and Hamedan Province.
8 February — Fewer providers affected by disruption
According to OIM data, the number of providers affected by the disruption decreased from 13 to 7.
On 8 February, TIC Director Hamid Fatahi and TIC board member Sajjad Bonabi claimed that the disruptions were caused by DDoS attacks originating from outside Iran. Authorities provided no further information to prove this claim, and our research was unable to gain insights into the source of the alleged attack.
A source close to the ICT Ministry told Filterwatch that “there is no specific evidence” due to be published about the origin of the DDoS attack.
According to the Arvan Cloud network monitoring system, Arsia Tech, Irancell, HiWEB and Respina were among the most severely affected providers. Later, on 16 February, Arvan Cloud itself was affected in a way that caused a number of its VPSs to be disconnected from the Internet and become limited to local websites, apps and services.
13 February — Severe disruptions recorded on two major providers
OIM provided an impact rating of 93.5 for the period of disruption in which Aria Shatel Company Ltd and Pars Online were almost completely disconnected from the internet for a very short period of time.
The fall in traceroutes on Aria Shatel and Pars Online demonstrates that these two providers were almost completely disconnected from the internet.
14 February — New Internet Exchange Point introduced
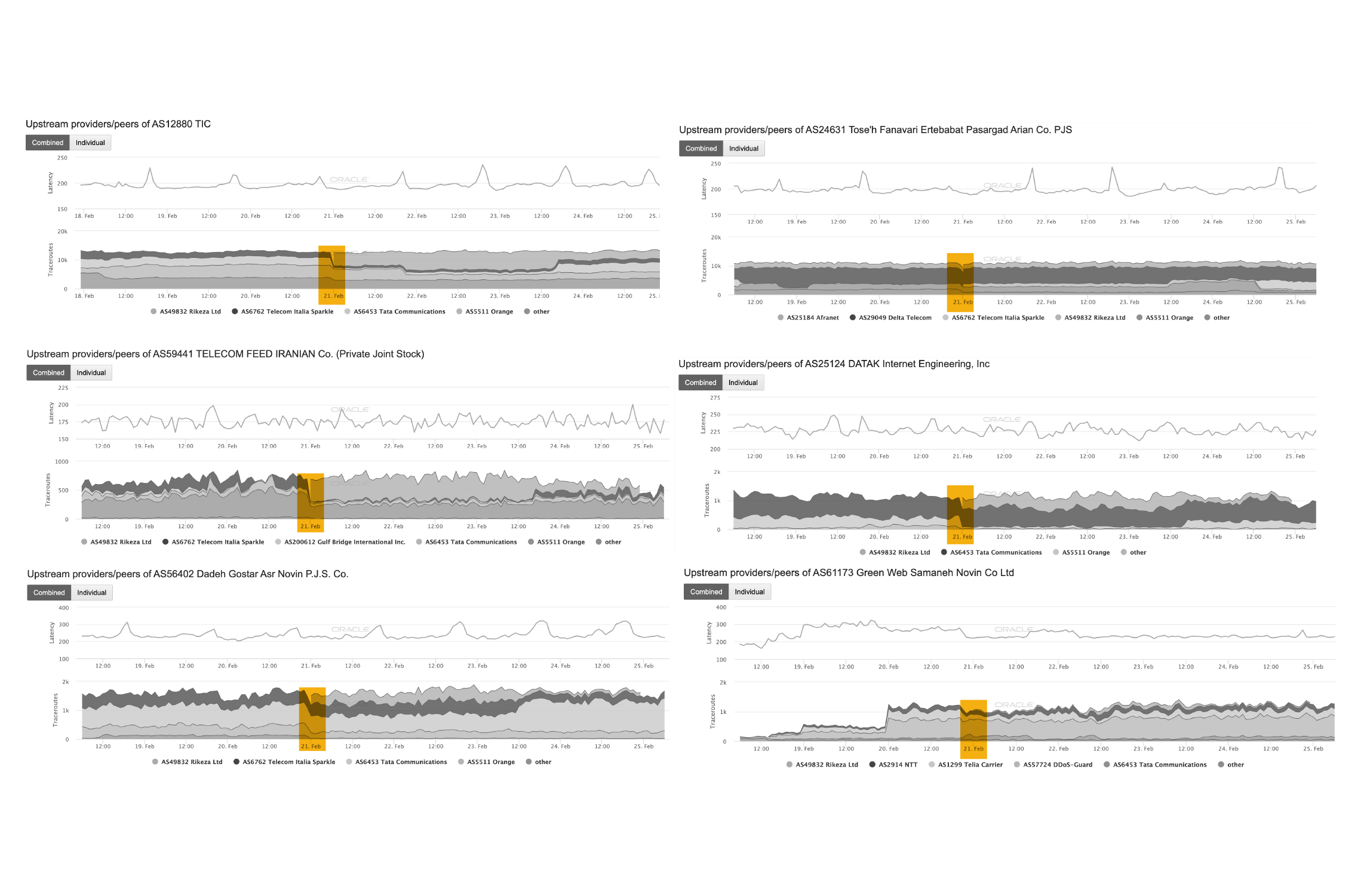
Significantly, a new Internet Exchange Point (IXP) was introduced, named ‘Rikeza Ltd’. Later, on 21 February, we observed significant data shifts from other IXPs to this new one.
16 February — Data centres disconnected from the Internet
Our research found that Arvan Cloud VPSs on MobinNet and Asiatech data centres were disconnected from the Internet. Later that day, Peivast reported that Arvan Cloud was affected by a DDoS attack originating from both inside and outside Iran. Our investigation found no evidence that other data centers were affected by this attack.
17 February — TIC blames domestic competitors for DDoS attacks
During the period of network disruptions between 2–17 February, Iranians officials repeatedly claimed that external hackers were responsible for sustained DDoS attacks.
But on 17 February, TIC board member Sajjad Bonabi, tweeted that: “the companies’ domestic competitors are likely to be the source of the attack.”
21 February — Traffic shifts to new IXP
According to the Tehran IXP website, the new IXP launched on 14 February has 16 members, including:
- Afranet AS25184;
- Asiatech AS43754;
- Avabarid AS51431;
- Fanap AS24631;
- Greenweb AS61173;
- Hiweb AS56402;
- Hostiran AS59441;
- Irancell AS44244;
- MCI AS197207;
- Mobinnet AS50810;
- Pars Online AS16322;
- Pishgaman Toseeh Ertebatat Company AS49100;
- Respina AS42337;
- Rightel AS57218;
- Shatel AS31549; and
- Iran Telecommunication Company PJS AS58224.
OIM also shows that there were shifts on TIC AS12880, AFROOZ AS43395, Fara Negar Pardaz Noor Khuzestan Co. AS49596, Soroush Rasanheh Company Ltd AS21341, Aryasat AS43343.
This shows that the Tehran IXP was added to the routing system of these providers. These shifts in traffic are highlighted in the visualisations below.


23 February — Unexplained disruptions to Irancell mobile data services
According to users’ reports, Irancell mobile data services experienced a number of brief disconnections (around two minutes at a time) in some parts of Tehran. Neither IranCell, nor the ICT Ministry offered any explanation for the service outages.
Our team believes that this disruption occurred as a result of the new Tehran IXP not yet being fully functional on IranCell AS44244. OIM data shows that Irancell AS44244 joined Rikeza Ltd on 21 February, but that it was subsequently disconnected on 25 February.
Our data also demonstrates that Rikeza itself suffered from service disruptions on 23 February, potentially explaining why this user was disconnected from the Internet.
26 February — Brief disruption incident affects over 50% of BGP routes
OIM data showed very brief internet disturbance in Iran which affected over half of all the BGP routes of Iran.
